Getting your pentests done is half the battle. Arguably the most important step is what comes after — fixing the discovered issues and preventing them from re-emerging again. So what does Pentest as a Service (PtaaS) change so teams can respond to findings quickly and effectively?
We’re glad you asked. Here are 4 things Matt Bromiley, SANS analyst and instructor, found particularly valuable in our PtaaS platform.
1. Prioritize faster with intuitive visual breakdowns
Having submitted a simple virtual machine on Azure for his pentest, Matt expected our team to discover issues that were not critical or requiring immediate attention. However, we found two vulnerabilities, one of which was highly critical. This needed fixing, and fast.

Many teams can find themselves in a similar situation, where they need to quickly adjust plans and draft a plan of attack in addressing critical findings. Aside from delivering the necessary information, a PtaaS platform like ours assists in another crucial area: making quick and informed decisions. Summaries pull all crucial information into one simple view so security can quickly piece together what to focus on first, and why. Having this information can help mobilize remediation teams faster.
2. Empower engineering teams with remediation context and guidance
Of course, simple high-level overviews are not enough. Remediation teams are mostly made up of engineers who might not understand why a certain issue is happening, and where exactly to find it. This lack of guidance in traditional pentesting models can severely delay remediation, as teams trudge through back-and-forth communication with their providers.
But as Matt discovered, a PtaaS platform here can truly shine. For example, in our platform’s Findings tab he was able to view all vulnerabilities validated and cross-checked by the lead pentester, and access more in-depth technical information about the issue on the individual Finding page. Here, he found detailed context from the pentesters including a description, a URL showing where the vulnerability was found, and a Proof of Concept with supporting screenshots.

Cobalt thought ahead and ensured that each finding reported in the test is properly documented with examples and a proof of concept. 〜 Matt Bromiley, SANS analyst and instructor
What’s more, we pair each finding with context as to why it has a certain criticality level, and what exact steps remediation teams can do to address the problem.

3. Improve remediation workflows with issue tracking integrations
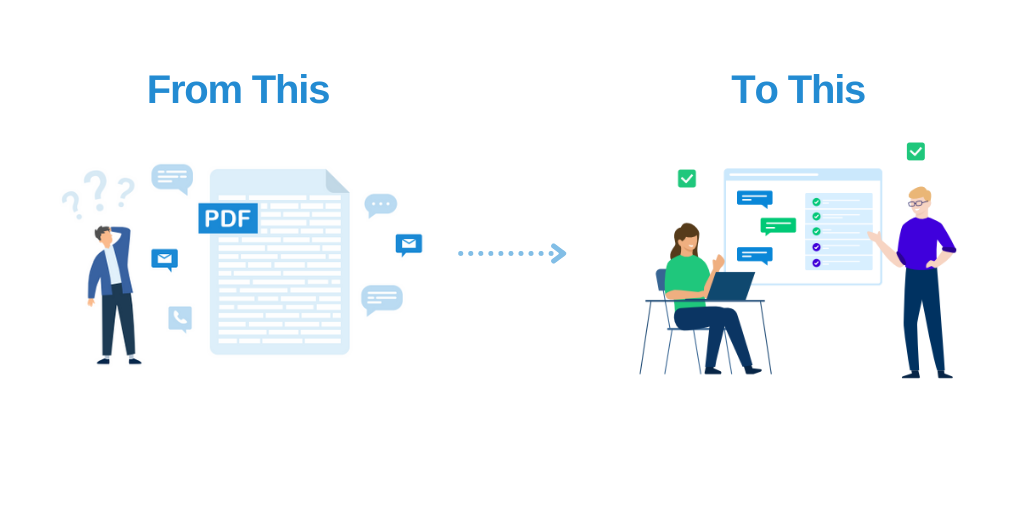
Here’s a complaint we’re sure your remediation team has raised: workflow inefficiencies. As more organizations have adopted DevOps workflows, traditional pentesting’s infamous PDF report ends up proverbially collecting dust in people’s inboxes. Issues get delayed because they’re not integrated into boards or sprints.
Some security teams put in the work to break findings down into tickets, but even that can be automated. Our platform nips the problem in the bud by rethinking how the provider can remove this issue. As soon as our pentesters record a new issue in the platform, security can send it straight to engineers’ spaces with our Jira and GitHub integrations.
Matt described this as “an extremely valuable feature and integration,” especially coupled with the last point we want to bring to your attention: you can validate fixes for free. Every pentest with Cobalt includes a free retest, regardless of scope or asset type.

By immediately taking penetration testing findings and converting them to issues, Cobalt established accountability to ensure that we fixed our weaknesses. Furthermore, included in the penetration test, is the ability to retest a weakness or vulnerability. 〜 Matt Bromiley
To read the full SANS review of Cobalt's PtaaS platform and learn about more features, download the white paper. Or if you’re ready to chat with us, why not request a demo call to explore more benefits of Cobalt’s Pentest as a Service (PtaaS) platform?